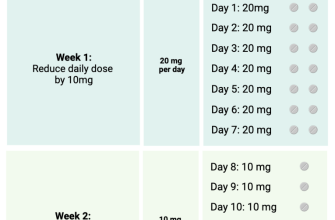
Explore the 2053 med direct platform for proactive health management. We offer personalized plans based on your genetic predispositions and lifestyle, providing actionable steps to improve your wellbeing. This involves detailed analysis of your health data, which is always kept secure and confidential.
Expect customized recommendations, including dietary advice tailored to your unique metabolic profile. Our system leverages advanced algorithms to analyze your data and predict potential health risks, allowing for early intervention and preventative measures. We integrate seamlessly with your existing healthcare providers, offering a holistic approach to your care.
Registration takes less than five minutes. After completing a brief health assessment, you’ll receive your personalized health plan within 24 hours. This plan includes regular check-ins with our team of certified health specialists, ensuring you have the support you need to meet your health goals. Contact us today to begin your journey towards a healthier future!
Patient Eligibility Criteria and Enrollment Process
To enroll in the 2053 Med Direct program, you must be a resident of the United States, aged 18-65, and hold a valid Social Security number. Your annual household income should not exceed $75,000.
Pre-existing conditions are generally covered, but certain exclusions apply. Review the detailed exclusion list on our website. Submit your application online using our secure portal.
Required documents include: proof of residency, ID, and income verification. You can upload these documents directly during online registration.
Processing time: We aim to process your application within 7-10 business days. You will receive an email notification once your enrollment is confirmed.
Following approval, you’ll receive your personalized 2053 Med Direct ID card within 14 days. This card grants you access to our network of providers.
Need help? Contact our support team at 1-800-MED-2053 or visit our FAQ page for answers to frequently asked questions.
Technological Infrastructure and Data Security Measures
Deploy a multi-layered security architecture incorporating firewalls, intrusion detection systems, and regular vulnerability scans. This proactive approach minimizes risk. Prioritize zero-trust network access, verifying every user and device before granting access to sensitive data. This model enhances security significantly.
Data Encryption and Storage
Implement end-to-end encryption for all data transmissions and utilize robust encryption algorithms, such as AES-256, for data at rest. Choose cloud storage providers with strong security certifications like ISO 27001 and SOC 2. Regularly audit your encryption keys and ensure compliance with all relevant regulations.
Access Control and Monitoring
Employ role-based access control (RBAC) to limit user privileges based on their responsibilities. This reduces the impact of potential breaches. Continuously monitor system logs and network traffic for suspicious activity; employ threat intelligence feeds to proactively identify and mitigate potential threats. Consider implementing security information and event management (SIEM) systems for centralized log analysis and threat detection. Real-time anomaly detection provides immediate alerts on unusual behavior.
Incident Response Planning
Develop a comprehensive incident response plan detailing procedures for handling security breaches. This should include steps for containment, eradication, recovery, and post-incident analysis. Regularly test the plan via simulated attacks to ensure effectiveness and identify weaknesses. Train staff on security protocols and awareness to quickly identify and report potential threats. This is a key factor in minimizing disruption.
Regular Updates and Maintenance
Maintain all software and hardware with the latest security patches and updates. This reduces vulnerabilities. Conduct regular security assessments and penetration testing to identify and address security weaknesses before they can be exploited. Employ a robust backup and recovery system ensuring minimal data loss in case of a failure or attack. Data backups should be stored securely and off-site.